I recently had an all-too-common request: "who deleted a folder from a Shared Mailbox?".
Technically you can audit these actions in M365 Purview/Exchange Admin Audit log, but it's cumbersome and takes forever...you know when you start a compliance search and hit refresh dozen times and it sits there in a "starting" state?
This is the method I've used for years before MS added the "audit 'move' for delegates" setting to mailboxes and it's still my go-to method over auditing. The reason being that auditing Shared Mailboxes can be hit or miss, and you can't easily tell where an entire folder was moved to; works fine for single items.
A faster, cleaner, way is to get the list of users who have Full Access into a CSV and pipe that in the Exchange Management Shell (EMS) to find the "missing" folder.
The default way shared mailboxes function is: whoever deleted a folder/item, it goes into their Deleted Items folder, not the Shared Mailbox Deleted Items...unless you've done a registry hack to change it (which is only feasible if you have a handful of users).
In my environment, we use Security Groups to assign Full Access, so I'll show you how to grab that user list, but the method remains the same if you assign users one-by-one as well.
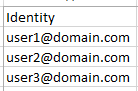
Create a CSV with "Identity" as the header and the email addresses below:
$DL = "DL"
Get-DistributionGroupMember -Identity $DL | Select primarysmtpaddress | Export-CSV "members.csv" -NoTypeInformation
**Note** Change "DL" to the distro you're working with.
Once you have your CSV exported, change the header to "Identity" like above.
Then, run:
import-csv filename.csv | foreach {Get-MailboxFolderStatistics -Identity $_.Identity | Where {$_.Name -eq "Margaret"} | Format-Table Identity,ItemsInFolderAndSubfolders,FolderAndSubfolderSize -AutoSize}
**Note** Change filename.csv to your CSV and "Margaret" to the name of the folder you're looking for.
It will spit out who has that folder in their mailbox:
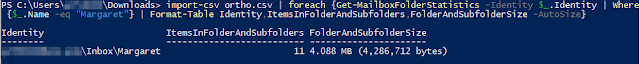
Notice how it shows the folder under User\Inbox\Foldername path? The problem user inadvertently moved the folder into her Inbox. If they deleted it, it would show User\Deleted Items\Foldername
Caveat: If the user deleted the folder and emptied their Deleted Items folder, you're out of luck recovering the entire folder. You have do to some more PowerShell magic to recover those and that's beyond the scope of this article.
Now, you can contact that user and yell at them to MOVE THE FOLDER BACK!